Managed Detection & Response
24/7 security monitoring and response, giving you peace of mind whilst you sleep at night…
Seamless Integration, Uninterrupted Operations: MDR for Modern Businesses
Our global security team delivers proactive threat research, incident response, threat hunting and optimisation around the clock.
Our Service
Want 24/7 SOC team access? Our MDR service detects and neutralises threats, saving your resources. Gain full visibility of your defences.
Key points:
- Fully managed Detection and Response service that aligns with ISO27001, NIST Cyber Essentials, MITRE ATT&CK and Kill Chain security controls.
- 24/7/365 – Global Security expertise to investigate incidents and neutralise malicious threats fast.
- Threat coverage to detect and neutralise Ransomware and Phishing attacks.
- End-to-end automation across the lifecycle.
- Real-time reporting that measures your risk and provides recommendations to increase the maturity of your security programme.
Watch our 2 Min Demo

Like what you see in the demo?
Why not...
Our Service
Our MDR is ideal for businesses that need round-the-clock security monitoring but prefer not to invest in their own SOC. Core to Cloud’s philosophy of working with our customers as partners mean that our security specialists become a natural extension of your IT team. This close working relationship allows us to understand the dynamics of your business and IT environment and collaborate on making continuous improvements.
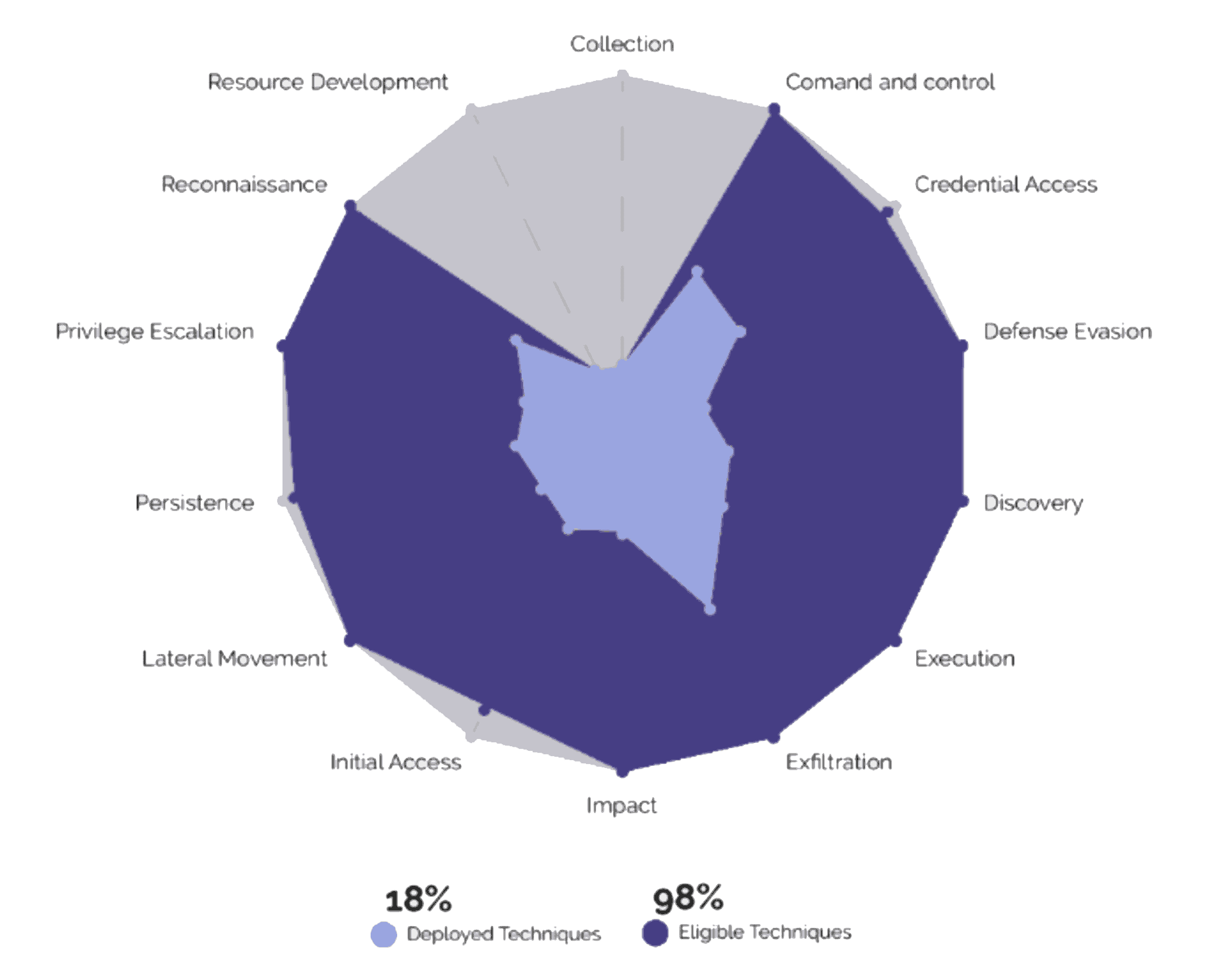
Core to Cloud MDR will deliver 24 x 7 security operations, monitoring and response services. This will manage the entire security lifecycle from the deployment of detection content to delivering high-fidelity detection capabilities across your organisation. This is mapped to your business outcomes and adopted cyber frameworks such as MITRE ATT&CK.
For each in-scope data source, we will review the current logging level to ensure appropriate visibility can be sought without the need to forward all data. Where required, Core to Cloud will advise the organisation on changes that will increase the level of visibility from the data source to drive a robust security posture without significant increases in data consumption.
The Solution is fully inclusive of the Core to Cloud IBM Q-Radar SIEM which by default is scoped to meet your requirements without providing any surprises.
For superior visibility, we would typically recommend connecting:
- Internal / Boundary FW’s
- IDS/IPS
- Domain Controllers
- Remote Access (VPN)
- Critical Servers
- Web Proxy
- AV
- Email Security
This provides a functional level of detection capability across the attack lifecycle that can be built upon with additional log source types and additional content rules.
The service is built on the following Key Principles:
- Leverage your existing technology or provide new tools.
- Unified platform across the security lifecycle.
- Visibility, Integration & transparency.
- Dedicated content developer to understand your unique threat landscape.
- Ad-hoc or custom rules that align with specific business outcomes.
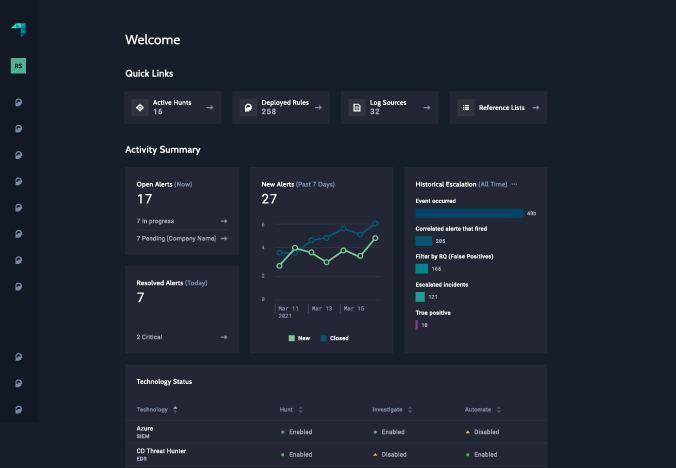
Outcomes:
- 400% improvement in threat detection in the first 90 days.
- 12 x increase in visibility.
- 35% reduction in costs through greater operational efficiency.
- Single platform provides a single pane of glass.
- Single source of service and support simplifies management and accountability.
- Access to industry specialists bringing knowledge and experience to you team.
- Improved ROI of existing security tools.
More than 80% of UK organisations experienced a successful attack in 2021/2022, according to Comparitech.
A huge number of businesses lost financially, dealt with breaches and data losses, and experienced many other unpleasant impacts of a successful cyberattack. These attacks are becoming more frequent and sophisticated and need dedicated 24/7 teams.
Are you struggling with deployment and implementation?
While many tools are available, security teams struggle with limited integration and a lack of visibility. Without this, teams are mired in manual processes, have slow response times, and are unable to implement automation confidently.
The result: decreased efficiencies lead to increased risk to the business.
You are probably wondering what the solution to this problem is…
Our MDR service provides around the clock security monitoring and response, so you can sleep better at night knowing that your business is being protected 24/7.
Core to Cloud’s MDR service is powered by 'GreyMatter Security Operations'. This will manage the entire security lifecycle from the deployment of detection content to delivering high-fidelity detection capabilities across your organisation. This is mapped to your business outcomes and adopted cyber frameworks such as MITRE ATT&CK.
What happens when we receive an alert?
1. When an alert activates, an analyst will begin an investigation process leveraging the data found in GreyMatter. The investigation is sourced and enriched by the integrated security tools (SIEM, EDR, Firewalls, etc) and GreyMatter Intel.
2. The path that will be followed (detailed further below) is that we will remove the noise through Tier 1 and Tier 2 with the specialists working on Tier 3 and reviewing the investigated alert with communication and response dependent on your local procedures which is reviewed during on-boarding.
3. We provide four tiers of severity levels for our alerts: Low, Medium, High, and Critical. We have an assigned default severity for each rule based on a proprietary formula that accounts for the kill chain phase, the quality of the log sources used in the rule, and the confidence we have that the scope of activity detected by the rule would “more often than not” detect malicious activity.
4. While these are default severity levels, they are not risk levels. As we continue to work with a customer and better understand their unique risks, we refine the severity and response levels/formats to ensure appropriate notification “how and when” they desire for each set of circumstances.
Next Steps: Dealing with today’s cyber threats requires a fundamentally different approach. Advanced malware exploits and other cyber-attacks will blow right by AV-based solutions in a fraction of the time it takes to get updated with the latest threat signatures. Furthermore, vulnerability exists in the gap between detection and response. Even if an attack is detected, lack of integration with incident response tools forces manual attempts to neutralise it.The key to effective endpoint protection lies in the ability to dynamically analyse and predict any threats behaviour and respond intelligently at machine speed – this is the essence of Core to Cloud’s service.
Contact our specialist team today
Get in touch to discuss tailored solutions for your cyber security and data protection requirements.